Somewhere in UK, a dialog box pops up on the screen of a Mac computer.
The user contacts me asking for an explanation I can’t quite provide. The same file (a downloadable version of Phone Story) works perfectly on my machine, also a Mac. It turns out the “file damaged” message is produced by Gatekeeper, an anti-malware feature of the new OSX Mountain Lion, which I haven’t bothered to install yet. Gatekeeper, by default, blocks every application that is not coming from the official Mac App store or from certified Apple developers.
I read a few articles about Gatekeeper, all of which are praising Apple for this long-sighted move to prevent the malware epidemic that plagues Windows users. More informal reactions from independent developers are along these lines:
“Yeah, it happened to me too. It’s a stupid message”
“No big deal, just go to the preferences panel and change the security settings”
“I agree with the goals of Gatekeeper, but that dialog box feels wrong. It’s very un-Apple-like.”
I certainly don’t expect the tech press to say anything against Apple, but I’m surprised by the lack of debate (outrage?) within Mac users and developers.
I’d like to make the case that this kind of trick is indeed very Apple-like, and that Gatekeeper is a reason for concern.
The Total Apple Consumer
It’s not too hard to understand why Apple’s innovations and branding strategy conquered millions of users in the last decade. But in order to turn groundbreaking products such as the iPod or the iPhone into monopolistic leverages, Apple had to go beyond mere product design and marketing to devise a smooth, seamless user experience among its platforms and devices. To become a vertically-integrated computing company and control hardware, software, content (iTunes / App Store), and personal data (iCloud) at the same time, Apple had to create a new kind of user, an ideal user which I’ll simply call: Total Apple Consumer.
The Total Apple Consumer is awesomely rewarded for its loyalty, while the impure one is punished. Using an iPod or an iPhone without adopting iTunes as mp3 player for your computer is a major annoyance. To be precise, it’s a carefully designed annoyance. Transferring files to an external device via USB doesn’t technically require a cumbersome online shopping application like iTunes. It’s the digital equivalent of those airport terminals that force you to walk though a labyrinth of duty-free shops in order to reach your flight.
Of course, things are way more functional and easy to manage when there are no junctions and no conflicts. It’s getting increasingly more appealing to adopt Apple’s monoculture, leaving behind an ecosystem of manufacturers, developers and services – often in competition between each other – like a PC+Windows set up. The risks of relying on one all-encompassing system (such as having your account hijacked) are negligible in comparison to a perfectly efficient, streamlined digital life.
A newspeak for the post-PC era
In the process of reshaping our relation with computing machines, Apple also had to exert control on computing language. For example: the concept of “synching devices” replaced the more intuitive and technically precise expression “copying files”. This brilliant semiotic move inscribes the notion of artificial scarcity into our daily interactions.
Synching obscures the very fact that you are copying files around. The idea that digital information can be freely duplicated and shared is dangerous – a gateway to piracy. What you are supposed to think instead, is that you acquired the right to consume a song, a video, or a piece of software, via a certain number of sanctioned devices and/or for a certain amount of time. And you shouldn’t really bother about how this affects your file system. In fact, your file system may not even exists.
Like the newspeak in George Orwell’s 1984, Applespeak is subtle and gradual.
Referring to applications as “apps” is not just a branding technique but a necessary linguistic reduction to conceptualize a lesser type of application. A little piece of software that sits in its little sandbox and doesn’t try to compete with the overarching platform.
For decades, digital artists and videogame developers have fought to elevate the status of software to that of any other cultural artifact. Apple overtly reject this idea.
The second paragraph of the guidelines for app developers reads:
We view Apps different than books or songs, which we do not curate. If you want to criticize a religion, write a book. If you want to describe sex, write a book or a song, or create a medical app.
An app is primarily a commodity and a functional tool. After all, freedom of speech doesn’t apply to screwdrivers or compasses.
Still, they’re not excluding the possibility of some kind of meaning emerging from an app, they just reserve the right to censor what doesn’t comply with their inscrutable moral standards:
We will reject Apps for any content or behavior that we believe is over the line. What line, you ask? Well, as a Supreme Court Justice once said, “I’ll know it when I see it”. And we think that you will also know it when you cross it.
The term “gatekeeper” in Information Technology is generally used as a negative term to refer to entities in a position of control over crucial services. In Applespeak, Gatekeeper becomes the friendly bouncer that knows when somebody “crosses the line”.
Designating all the applications that are not Apple-approved as “damaged files” to be trashed is an even bolder linguistic intervention. Users who want to decide what software runs on their machines have to change the default setting and go through another intimidating message.
Beware: the Internet outside Apple’s digital stores is a scary, scary place…
Boiling the frog
In terms of security, Gatekeeper is a remarkably lazy approach. Instead of making a “black list” of bad software like anti-virus programs generally do, Gatekeeper starts from a presumption of guilt and performs a “white list” check. If you sell through the Mac App store, paying a yearly fee and 30% of the revenues for this privilege, you are on the list. Unless, of course, your products violate their arbitrary guidelines.
You’d have to be the most clueless Apple believer to buy into this narrative. If developers’ certification was really the key to security, a third-party validation by companies in the business of detecting malware would be more appropriate.
A complementary approach could involve educating users to recognize suspicious files – which unfortunately it’s at odds with Apple’s tendency to strategically obfuscate the internal structure of their systems.
As depressing as it can be, it’s more logical to think of Gatekeeper as a step toward the exclusive control of content in that shiny post-PC era envisioned by Steve Jobs. The monopolistic App Store for iPhone and iPad turned out to be so profitable, it would be foolish for them to not extend the system beyond mobile devices.
Needless to say, Apple already has the capacity to block all non-approved software running on “their” machines.
Some Total Apple Consumers may welcome this as a another time-saving, stress-reducing service, but such a swift, uncompromising move is likely to cause an insurrection among power-users and software developers. That’s why they can only attempt a gradual shift. For now it’s just a security setting you can change but who knows what will happen with the next update. The message to developers is clear: if you make software for Mac you’d better look into this whole Mac Store thing, or you may suddenly be cut off.
Personal Computer = Personal Liberation
Techy people may find these remarks obvious. Apple’s 360º expansion strategy is rather transparent if you bother to observe it in perspective. But many computer users can’t even tell the difference between a browser and a search engine. They certainly aren’t going to mess with their System Preferences to make their computers “less safe”.
Why should we care about them? Shouldn’t we welcome more constrained systems for those who are so dumb as to not recognize malware and online scams? Isn’t the iPad the most appropriate device for the 21st century couch potatoes who only need to check their email, watch some cat videos, and post pictures on Facebook?
If we care about being surrounded by active, informed and empowered citizens, we should be concerned about Apple’s post-PC vision, and fight for the right to control the software that runs on our devices. Apple is on the front line of what writer and commentator Cory Doctorow calls The Coming War on General-Purpose Computing.
This isn’t an entirely new struggle. The first book about personal computers was written by Ted Nelson in 1974. Its title was Computer Lib/Dream Machines, a fist on the cover, with the emphatic call: “You can and must understand computers NOW”.
For pioneers like Nelson, the creative and political potential of computing machines and informational networks was immediately evident. The challenge was to make these machines available to everybody and promote a new kind of literacy.
The tyrants to overthrow were the centralized systems, namely: television and mainframe computers. It’s worth remembering that before PCs, people worked with “terminals” which functioned as input/output devices for central entities called mainframes. Systems administrators defined the policies and controlled the software.
These radical ideas of computing freedom were so influential that they became selling points for the emerging IT sector. The famous TV ad launching the first Macintosh computer in 1984 dramatized this antagonism, referencing Orwell’s dystopia:
Obviously, disruptive companies can’t stay disruptive forever. Investors demand increasing returns and impose an endless march of expansion and consolidation. Ultimately, every IT corporation strives to become Big Brother.
The Total Apple Consumers (which, again, are the ideal consumers that Apple tries to create) are the subjects of a mainframe model applied to the consumer-side. They store all their personal data in remote iClouds; purchase music, eBooks and newspapers from iTunes; find directions, stores and local services though Apple Maps; they dabble with apps made by Apple’s indentured developers; when tired of tapping and swiping touchscreens, they can enjoy a moment of relaxation, watching TV and movies through Apple TV.
Their post-PC devices could perhaps help them figure out what TV shows they should watch and which ones they should “move to the trash”; which websites are trustworthy and which ones are “damaged” and so on…
Once you control all points of entry to the digital realm, the possibilities are endless.
They who can give up essential liberty to obtain a little temporary safety, deserve neither liberty nor safety.
– Benjamin Franklin

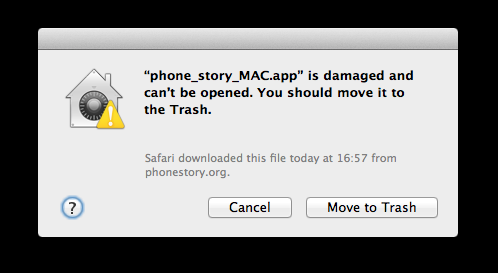

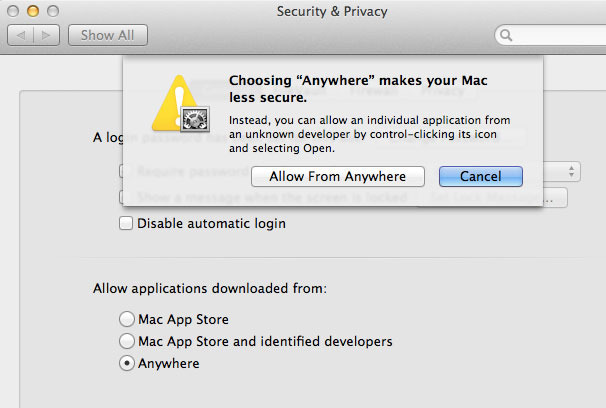

I’m with you 100%, apple don’t do anything like this for any other creative work; you don’t get a warning if you’re browsing photos taken by a non-apple-identified photographer, or listening to music performed by a non-apple-identified musician. why is software singled out?
I think it’s just like you say; alternative software is the biggest threat to apple’s ideal monopoly.
Because music and photos can’t install key-loggers or steal user’s financial information, that’s why.
Hey, don’t bring me into the discussion. That makes for bad shoutey complainey people to have nothing to do any more.
The hell they can’t – malware hiding in pictures has been done.
Along the same lines as Applespeak, I think this highlights some of the other problems with current tech discourse. Although we talk about concepts like “digital natives” and “ubiquitous computing,” this seems to gloss over the fact that we are still a long way from the kind of digital literacy that Ted Nelson was advocating almost 40 years ago.
The first super weird thing is that an OS X developer somehow hadn’t heard about Gatekeeper. I’m not sure how that happens. This isn’t news; it was common knowledge that this was a thing in Mountain Lion six months ago. Even I heard about it back then, and I don’t use OS X.
The second thing is that Paolo blasts Apple, but fails to provide a reasonable alternative for Gatekeeper. Historically, black lists of executable signatures for the purposes of security have been a terrible hack. It’s a constant race to keep up with malware authors. Signed packages are absolutely the future. Linux distributions have been doing it for eons. Part of problem is that the Unix permissions model doesn’t really work as well as we’d like. We used to mostly want to protect users from each other. Now we mostly want to protect users from their applications.
Apple could stand to improve their implementation, but they’ve got the right basic idea. All apps should be signed. Maybe we should talk about who should be allowed to provide the signing keys, instead.
What problem does Gatekeeper solve, exactly? Why does Paolo have to propose a reasonable alternative to something that *isn’t necessary* and has yet to be shown to achieve any measurable improvement for people who actually use computers?
It’s one thing to sandbox applications and do other things to protect users from malicious software, but if somebody intentionally downloaded a .app – or god forbid, paid for it without using the Mac App Store – they probably intended to run it. To respond to this extremely clear intent with a cryptic error dialog with no direct route to actually run the application is moronic. An Apple-maintained application whitelist where the only requirement to get a signing cert is $99 won’t do anything to protect people unless Apple somehow manages to identify and revoke all malware before it actually runs on users’ machines.
Linux packages and signing are nothing like Gatekeeper. Windows also has had an established solution for this problem for ages (called Authenticode) that historically ‘protects’ users in a less heavy-handed and cryptic manner, with signing certificates available from various sources after a short vetting period.
If you’re specifically worried about keyloggers, why not solve that problem by requiring the user to enter a password to perform actions that require root privileges? OS X is unix, isn’t it?
I don’t know, you just keep writing this well, Paolo, and you can convince me of going libertarian if you like. Great decision to start this blog, your voice feels like just what the videogame world needs right now.
Most apps will not see the “app is broken” dialog, instead they see an “app cannot be launched because it is from an unknown developer” dialog, which can be circumvented with the contextual menu. I’m not sure what triggers the “broken” variant, but it’s not normal. You might want to look into that. Is your app Java?
Yes, I’m aware that it’s not the “normal” message. But it’s very common, there are hundreds of support requests on forums all around the Internet. I’m looking into the issue and I’ll post an update as soon as I figure out what exactly triggers it.
The “damaged” message happens when an application has a security signature, but Gatekeeper thinks it isn’t valid. This happens if it’s been modified after signing – the usual “good program gone bad” that codesigning is meant to detect. Unfortunately, Gatekeeper does its signatures differently somehow, so installers that were correctly signed before Gatekeeper came on the scene now fail validation are are flagged as infected. Brilliant.
It’s amusing that people are dragging Linux into this. Yes, distros package software then sign it. It’s the whole of our appointed reason for existence in the first place. Heck, at some level, a lot of us are probably bigger hardasses than Apple. The flipside, of course is that we don’t deny people their rope when they relentlessly pursue hanging. I can think of no package manager that prevents users from installing out-of-tree packages. People complain all the time about how there are “so many _different versions_! “, but that’s not really true. What we have a lot of are approaches to packaging the software people want and need on top of the same basic stack.
Suffice to say, I think Apple has missed the point of blessed repos: quality assurance. You’re right to be concerned even outside the shadiness of a sterile ecosystem.
Of course, Apple’s claim that they don’t censor (“curate”) books is a lie.
While I can understand some valid non-DRM reasons for such a system (such as keyloggers and malware) I think this a pretty ham-fisted solution to the problem.
Allowing this as a feature is fine, but it should default to off, or be a prompt when the OS is installed. Like the infamous User Access Control, which started in Windows Vista, it simply fixes a security problem by locking down the system and severely restricting it’s ability to perform its intended function.
This feature makes sense for a public computer, for your kids’ user accounts, and for someone who doesn’t know much about computers and isnt installing software, but for most users, this is far too restrictive to be useful.